External Service Providers and CMMC
On Thursday August 3rd, 2023 the Office of Information and Regularly Affairs (OIRA) sent the CMMC world into a frenzy by inadvertently publishing what appeared to be updated CMMC Model Overview, CMMC Assessment Guide, CMMC Scoping Guide, and CMMC Hashing Guide documents. OIRA has since taken down the documents, but not before the public were able to download them and review.
We were able to download and analyze the above-mentioned documents. Keep in mind, these documents are not official and OIRA and/or D0D may make changes to them. With that said, here are the top three key takeaways from analyzing the documents.
1. CMMC Level 2 Scoping Guide
There were some major changes from the currently published CMMC Level 2 Scoping Guide (version 2.0) versus the updated CMMC Level 2 Scoping Guide (version 2.1). One of those changes was in the ‘External Service Provider Considerations’ section.
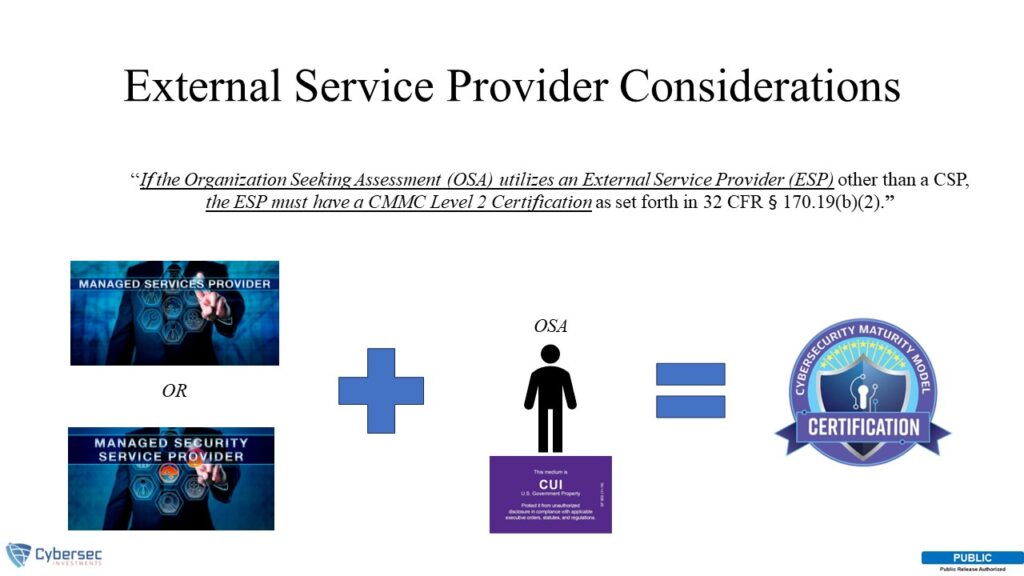
It states, “An External Service Provider (ESP) can be within the scope of CMMC requirements if it meets CUI Asset and/or Security Protection Asset criteria. To be considered an ESP, data (specifically CUI or Security Protection Data, e.g., log data, configuration data) must reside on the ESP assets as set forth in 32 CFR § 170.19(d). If the OSA utilizes an ESP other than a CSP, the ESP must have a CMMC Level 2 Certification as set forth in 32 CFR § 170.19(b)(2).”
What does this mean in plain English? If your managed service provider (MSP) and/or managed security service provider (MSSP) is handling your environment’s log data, configuration data, etc., then they will need to have a CMMC level 2 certification.
2. CMMC Level 2 Scoping Guide
Up until this point, the Office of the DoD Chief Information Officer (CIO) listed the CMMC Level 3 Assessment Guide as ‘under development’. This document provides insight on what controls organizations seeking certification will need to meet. It appears the DoD has selected 24 of the 35 enhanced security requirements from NIST SP 800-172 into the newly updated CMMC Level 3 Assessment Guide. These include security requirements such as having a security operations center, having a cyber incident response team, performing penetration testing, and more.
3. CMMC Level 3 Scoping Guide
Lastly, just like the CMMC Level 3 Assessment Guide, there previously wasn’t a CMMC Level 3 Scoping Guide. This is a new document that we’re all seeing for the first time.
One of the most telling lines in the document located in the ‘External Service Provider Considerations’ section states, “To be considered an ESP, data (specifically CUI or Security Protection Data, e.g., log data, configuration data) must reside on the ESP assets as set forth in 32 CFR § 170.19(d)(2). If the OSC seeking CMMC Level 3 Certification utilizes an ESP, other than a CSP, the ESP must have a CMMC Level 3 Certification as set forth in 32 CFR § 170.19(c)(2).”
What does this mean in plain English? If your managed service provider (MSP) and/or managed security service provider (MSSP) is handling your environment’s log data, configuration data, etc., then they will need to have a CMMC level 3 certification.
Currently, external service providers are not eligible for the DoD’s Joint Surveillance Voluntary Assessment (JSVA). However, they can demonstrate a high level of assurance to their clients by obtaining a NIST SP 800-171 3rd Party Letter of Attestation.
We hope you found this quick analysis helpful. If you have any questions, please contact us at info@cybersecinvestments.com or give us a call at (800)960-8802
Recent Posts
- How Technology Is Transforming C3PAO Assessment Process
- Top Mistakes That Can Delay Your CMMC Assessment And How To Avoid Them
- The Hidden Value Of Professional CMMC Certification Services For DoD Contractors
- CMMC Compliance Made Practical: Strategies That Actually Work For Contractors
- How CMMC News Is Changing The Rules For Government Contractors
Search
Recent Comments
Recent Posts
- How Technology Is Transforming C3PAO Assessment Process October 15, 2025
- Top Mistakes That Can Delay Your CMMC Assessment And How To Avoid Them October 14, 2025
- The Hidden Value Of Professional CMMC Certification Services For DoD Contractors September 30, 2025
- CMMC Compliance Made Practical: Strategies That Actually Work For Contractors September 10, 2025
Archives
- October 2025 (2)
- September 2025 (4)
- August 2025 (2)
- July 2025 (6)
- June 2025 (8)
- April 2025 (9)
- March 2025 (5)
- February 2025 (1)
- January 2025 (8)
- December 2024 (7)
- October 2024 (2)
- March 2024 (1)
- February 2024 (1)
- January 2024 (1)
- December 2023 (1)
- August 2023 (1)
- July 2023 (1)
- June 2022 (1)
- April 2022 (1)
- November 2021 (1)
- June 2021 (1)
- May 2021 (1)

Recent Comments