CMMC Or CMMI For Your Compliance Strategy? Here’s How to Decide
Did you know cybercrime threatens economic and national security by stealing various businesses’ confidential information and intellectual property?
The FBI believes that hostile cyber activities harmed the U.S. economy by $16 billion in 2024. In addition, the same year, an increase in cyberattacks was observed, with many employing advanced strategies and tactics, including breaches and ransomware of specific infrastructure. This certainly highlights the utmost necessity of deploying cybersecurity measures.
Malicious cyber actors have targeted and continue to target the Defense Industrial Base (DIB) sector, as well as the Department of Defense’s (DoD) supply chain. These attacks target not only large prime contractors but also subcontractors at the lower levels of the DoD supply chain.
Many of these subcontractors are small businesses that provide valuable support and innovation. Overall, the DIB sector is made up of over 220,000 companies that process, store, or transmit Controlled Unclassified Information (CUI) or Federal Contract Information (FCI) in support of the warfighter, as well as contribute to the following:
- Research
- Engineering
- Development
- Acquisition
- Production
- Delivery
- Sustainment
- Operations
The overall loss of intellectual property and regulated unclassified information from the DoD supply chain can undermine U.S. technological advantages and innovation while dramatically increasing the risk to national security.
What Does The DoD’s Collaboration Signify?
As part of a multifaceted effort to improve the security and resilience of the DIB sector, the DoD is collaborating with multiple industries to implement safeguarding obligations for the following types of unclassified information along the supply chain:
- Federal Contract Information (FCI) is defined in 32 CFR §170.4 and 48 CFR 4.1901.
- Controlled Unclassified Information (CUI) is specified in 32 CFR § 2002.4(h).
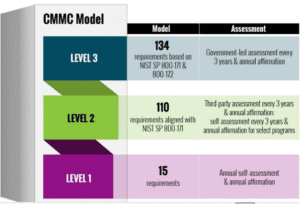
To that end, the Office of the Under Secretary of Defense for Acquisition and Sustainment (OUSD(A&S)) and DoD Chief Information Officer (CIO) collaborated to create the Cybersecurity Maturity Model Certification (CMMC) with DoD stakeholders, University Affiliated Research Centers (UARCs), Federally Funded Research and Development Centers (FFRDCs), and the DIB sector.
However, when using the CMMC paradigm, an organization can achieve a given CMMC level for its entire business network or a specific enclave(s), depending on where the information to be safeguarded is processed and kept.
Why Is There an Urgency for Cybersecurity?

Compliance today is a strategic need rather than a check-the-box necessity. Two frameworks that come up often in these discussions are the Capability Maturity Model Integration (CMMI) and the Cybersecurity Maturity Model Certification (CMMC).
Although both maturity models enable companies to move from ad hoc, chaotic activities to organized, optimal operations, they differ fundamentally in scope, focus, regulatory consequences, and implementation results.
Deeply ingrained in cybersecurity, especially the protection of Controlled Unclassified Information (CUI), CMMC is a contractual need for defense contractors engaged with the U.S. Department of Defense (DoD). Conversely, CMMI started as a software process improvement model and has since developed into a more general framework directing companies in many sectors toward operational excellence.
Selecting CMMC or CMMI (or figuring out how they might complement one another) should be done with strategic alignment, corporate objectives, and regulatory exposure in mind. This paper gives a thorough analysis of both models together as well as ideas on how companies may choose which road or mix of paths fits their compliance approach.
Interest in how the Cybersecurity Maturity Model Certification (CMMC) differs from other models, like the Capability Maturity Model Integration (CMMI) and the National Institute of Standards and Technology (NIST) Cybersecurity Framework, has increased since its recent release.
We’ll give a quick rundown of each model and its differences today. Prior to discussing CMMC vs. NIST or CMMI vs. CMMC, let’s discuss standards and maturity models.
What Constitutes a Standard?
It is about security and not CMMI vs. CMMC.
Organizations utilize standards and maturity models to assess their resilience and strength. However, they don’t produce security on their own. They don’t develop technology or procedures. They serve as a checklist.
Making sure that an organization’s cybersecurity infrastructure is not only compliant but also flexible enough to respond to changing threats is a crucial component of information security standards. Many companies place too much emphasis on following checklists at the expense of making sure their overall security posture is strong.
Attempting to “build to the checklist,” behaving like their checklists are a set of requirements, can land organizations in hot water. Although it might be the truth in some situations (several holistic cybersecurity models claim to lay the groundwork for a highly secure system), it ignores the fact that each system is different.
The Disparities Comparing CMMI & CMMC
All things considered, CMMC and CMMI cover some prudent practices, but they are somewhat separate topics.
Keep in mind that regulations and the world are always evolving. Therefore, we may see entirely new standards in the upcoming year.
1. CMMI
The Software Engineering Institute (SEI) of Carnegie Mellon University (USA) governs the Capability Maturity Model Integration (CMMI) process improvement framework, which was developed over 20 years ago. CMMI is sponsored by the United States government (particularly the Department of Defense) and used by organizations of all sizes.
CMMI is a process improvement framework designed to serve various application contexts. Moreover, there are three models based on the CMMI framework:
- CMMI for Development is a paradigm for managing and improving processes in software development firms.
- CMMI for Acquisition is a methodology for enterprises that must initiate and manage the acquisition of products and services.
- CMMI for Services is a process paradigm that helps organizations deploy and manage services.
By definition, CMMI for Development is the best option for process improvement in data warehouse development. It can improve the efficiency of software product development processes (such as a data warehouse), including those for planning, managing, and controlling development operations.
The CMMI for Development standard includes best practices from successful development organizations as well as the experiences of software quality professionals.
2. CMMC
CMMC is a new cybersecurity certification program created by the Department of Defense (DoD) to enhance the security of its contractors and suppliers. Besides, it expands the existing CMMI framework by incorporating particular cybersecurity criteria.
Organizations intending to do business with the DoD must receive a CMMC certification at one of three levels, depending on the sensitivity of the information they would handle. Conversely, obtaining a CMMC certification is critical for federal contracting compliance professionals to ensure they meet DoD cybersecurity regulations.
Structural and Strategic Contrasts: CMMC Vs. CMMI
Structurally, CMMC and CMMI both adopt a mature model approach, promoting ongoing development. However, the intention and use of these models differ greatly as well.
CMMC is somewhat limited in targeting the protection of sensitive data. Its objective is to apply a defined set of cybersecurity measures, lowering the possibility of data loss and compromise. Whether or not that job concerns information security, CMMI functions as an organizational compass for enhancing how work is done.
CMMC systematically facilitates regulatory compliance. It is time-sensitive, enforceable, and contract-driven. Ignoring its standards could cause one to be disqualified from federal programs. On the other hand, CMMI enables business process optimization, cost control, and long-term capability development, strategic in a different sense.
The efforts at implementation also vary. CMMC sometimes requires a higher initial cost in technical protections, documentation, and audit-ready capability. It can call for incident response playbooks, network segmentation, encryption techniques, and multi-factor authentication.
Conversely, CMMI sometimes emphasizes establishing performance baselines, defining and measuring processes, and controlling internal variance.
While CMMC is essentially about cyber defense, CMMI is related to operational effectiveness.
Why does CMMC Need Precedence for Defense Contractors?
CMMC is not negotiable for any company managing CUI with the Department of Defense. It is a gating factor deciding contraction eligibility. Under CMMI, a company’s internal processes may be simplified, but failing to satisfy CMMC requirements will prevent access to government defense projects.
CMMC also offers statistically valid proof of cyber readiness. Organizations cannot afford to view cybersecurity as a passive activity in a world where ransomware assaults nation-state threats are growing, and IP theft is becoming common.
By means of mandated assessments, CMMC fosters responsibility and thereby elevates the standard for every contractor.
Can CMMC and CMMI coexist?
Though they differ, CMMC and CMMI are not exclusive to one another. In all fairness, CMMI can be a basic enabler for putting CMMC policies into use and upkeep.
CMMI’s emphasis on documentation, metrics, and ongoing improvement, for instance, directly helps CMMC compliance to be sustained over the long run. While CMMC may provide the controls a company needs, CMMI can help to guarantee that such controls are regularly used, audited, and evolved over time.
Companies that have already made investments in CMMI could find themselves in a position to advantageously seek CMMC accreditation. Their current change management practices, internal audits, and process discipline will help speed up the CMMC implementation.
Conversely, CMMC can provide cybersecurity rigor to CMMI-driven process environments that might otherwise ignore data security concerns.
Which Model Should You Give Top Priority?

The choice between CMMC and CMMI should be based on internal capabilities, client base, risk exposure, and the regulatory environment of your company.
CMMC is the only starting point, whether you manage CUI or are part of the Defense Industrial Base. Under CMMI, no internal process improvement will replace the cybersecurity emphasis of CMMC.
Federal doors stay locked without CMMC.
CMMI may offer the best return if your company handles sensitive government data, targets to maximize delivery or lower cost variance and serves private-sector customers.
Both systems may be required in hybrid situations—that is, defense subcontractors with commercial verticals. In these situations, CMMC should be used first to guarantee compliance, followed by CMMI to ingrain long-term process excellence.
A Consistent Compliance Plan
The boundaries between cybersecurity, operations, and compliance keep blurring as digital transformation speeds forward. Selecting between CMMC and CMMI calls for more risk tolerance, strategy alignment, and regulatory exposure than just a matter of framework.
CMMC is your first and most important compliance need, whether your goal is to cater to the federal government or already manage sensitive military data. Without it, your company is not just susceptible; it is invisible in the federal procurement system. As a consequence, a multitude of organizations are deploying a 3rd Party Assessment Organization that possesses years of experience in the field of cybersecurity.
CMMI should be considered a process partner to CMMC if your long-term plan calls for providing excellent services, lowering cost overruns, and attaining internal consistency. The finest compliance plans are not developed inside silos. They use CMMC’s strengths as well as CMMI to build a mature, secure, compliant, and future-ready company.

Recent Comments