Early Steps For Defense Contractors Preparing For CMMC Audits
Cyber threats have reached an unprecedented level in the defense industrial base (DIB), including state-sponsored attacks and other advanced breaches that are a major threat to national security.
Hence, in a bid to ensure contractors handling Controlled Unclassified Information (CUI) implement consistent, verifiable cybersecurity standards, the U.S. Department of Defense (DoD) has come up with a structured framework: Cybersecurity Maturity Model Certification (CMMC).
CMMC 2.0, enacted in late 2024, places greater emphasis on accountability and third-party assessments. Despite industry awareness, several contractors have not yet formally aligned their systems with certification guidelines. As a matter of fact, 70% of firms have intended to undergo a third-party audit in the current year.
The consequences of delay are serious: loss of contract eligibility, loss of confidence by the client, and increased exposure to cyber threats. Contractors now face a pivotal moment.
Delaying compliance puts contracts and reputations at risk, whereas timely action means obtaining a competitive advantage. Let’s walk you through the foundational steps to prepare for CMMC audits, examine the common pitfalls of compliance, and highlight how to turn early preparation into a strategic cybersecurity asset.
The New Normal: Proactive Compliance Is No Longer Optional
Cybersecurity is no longer a back-office concern; it is now mission-critical for defense contractors. Gone are the days when compliance was a checkbox exercise or something to be concerned about just before a contract renewal. The new reality demands a proactive approach.
This shift has been brought about by real-world breaches. The SolarWinds attack has shown how a single vulnerability in a trusted IT vendor could compromise government systems.
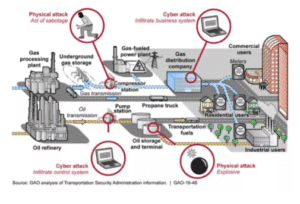
The Colonial Pipeline attack caused substantial disruption to vital infrastructure and highlighted the national domino effect of cyberattacks. These events not only made headlines—they became catalysts for change.
This has caught the attention of contractors in the defense supply chain. In a recent survey by Deltek, 45% of mid-sized contractors have already engaged external consultants to begin preparing for CMMC audits, indicating widespread urgency and commitment to compliance. It is a figure that indicates even higher momentum at the industry level, and it is making waves in the most recent CMMC news cycles.
Compliance does not just mean avoiding penalties. It enhances your defensive capability, boosts your reputation with government clients, and also raises your bid-winning possibility.
Understanding CMMC Levels & What They Mean For You
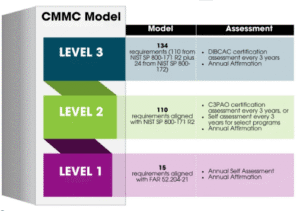
CMMC 2.0 has set three levels of compliance in cybersecurity. Each level is customized to suit the sensitivity of information a contractor works with.
Level 1: Foundational
This entry-level tier is targeted at basic cyber hygiene and addresses 17 practices that protect Federal Contract Information (FCI). It is intended to meet the needs of contractors who are not dealing with sensitive defense data but still need to protect general federal information.
Level 2: Advanced
The level is targeted towards the firms dealing with Controlled Unclassified Information (CUI) and aligns with NIST SP 800-171, which mandates 110 security practices.
Pro tip: Contractors working with CUI now require a formal certification by a C3PAO (Third-Party Assessment Organization) to achieve the requirements of a Level 2 audit.
Level 3: Expert
Exclusive to the most sensitive contracts, Level 3 builds upon Level 2 with additional controls from NIST SP 800-172. Such requirements are yet to be formulated but are likely to encompass government-sponsored assessments.
First Steps Defense Contractors Must Take Now
To stay abreast with CMMC compliance, start by evaluating your current cybersecurity position, visualize and fixing the loopholes before an official audit appears on your radar. Here’s where to begin:
1. Inventory Your Assets
It should start with data mapping. Identify every system, device, or cloud environment that stores, processes, or accesses Controlled Unclassified Information (CUI). If you cannot see, you cannot protect.
2. Conduct a Gap Assessment
Evaluate your existing cybersecurity practices against the 110 controls of NIST SP 800-171, the framework that is at the foundation of CMMC Level 2. This will expose you to your strong and weak points.
3. Assign Roles & Build a Team
Assign a cross-functional team or CMMC task force. This group must include IT, compliance, and operations stakeholders to harmonize the efforts and ensure accountability.
4. Build Your SSP and POA&M

The development of your System Security Plan (SSP) and Plan of Action & Milestones (POA&M) should not be left out for later. These are living documents that will direct you on your way to compliance and are required for audits.
The Risk Landscape: What Happens If You Wait?
Putting off CMMC compliance is not only risky, it’s potentially contract-ending. Defense contractors that fall short of cybersecurity standards will not be able to work on the DoD supply chain, irrespective of years of experience in government work. In many cases, this may imply losing millions of future contracts.
It is not just missed bids. Failure to meet the requirements of CMMC can also be a violation of DFARS clauses and, in particular, the requirements 252.204-7012 and 7019. This opens the door to severe legal and financial exposure, such as False Claims Act liability in the event a contractor knowingly makes a false attestation of compliance.
Consider this real-world example:
An 80-person aerospace parts supplier with $35 million in annual revenue neglected their CMMC Level 2 preparation—betting on the assumption that enforcement would start late in the year. With a focus on ERP migration and production backlog, cybersecurity took a backseat.
And then, one of their Tier-3 vendors, a 12-employee CNC shop, became the victims of a ransomware attack. There was a compromise of sensitive DoD-related documents that were shared over an unsecured Dropbox folder, such as CAD drawings, tolerances, and contract identifiers.
That violation triggered a DoD Supplier Risk Assessment, which identified the aerospace supplier as the source of the exposure due to the supplier not having encrypted Controlled Unclassified Information (CUI) and not using flow-down clauses in vendor contracts.
Its aftermath was quick. The supplier was dropped from their prime vendor list, lost more than a million in estimated revenue, and is now subject to potential False Claims Act scrutiny for handling CUI without meeting NIST SP 800-171 standards.
Even though they did not deliberately mislead the government, failure to comply while accepting federal funds left them vulnerable to constructive fraud allegations. This was more than a technical failure; it was a systemic one rooted in delayed action, weak supplier oversight, and misplaced trust.
Now, the company is fighting legal repercussions and reputation damage that it would have easily avoided.
Building a Resilient Cybersecurity Culture
Technology is just one half of a cybersecurity equation; your people and processes are equally important. Establishing an effective security culture implies inculcating cybersecurity awareness in your organization.
1. Prioritize Awareness Across the Organization
Each employee contributes to securing sensitive data. Consistent, role-based training prompts your team to recognize phishing attempts, securely deal with data, and act in response to evolving threats. Encourage a “report early, not late” mindset to catch issues before they escalate.
2. Reinforce with Strong Technical Controls
Enhance your training efforts with layered security controls. All systems should have multi-factor authentication (MFA), endpoint protection, and access restrictions. These protections mitigate the consequences of risk in case of human error, an unfortunate but common reality.
3. Build Accountability and Engagement
Ensure that cybersecurity is everyone’s responsibility. Form the habit of rewarding attentiveness, normalize the reporting of incidents, and allow employees to open up without any fear. An active team combined with sound processes delivers a proactive security posture as opposed to a reactive security posture.
Partnering With C3PAOs & Consultants: When to Bring in Help
To numerous defense contractors, CMMC compliance can be an arduous task that IT teams within the company might not have the time to manage, the experience to manage, or the resources to manage.
Under these circumstances, you can engage a Certified Third-Party Assessment Organization (C3PAO) or a trusted consultant to help you up your readiness curve and mitigate the possibility of expensive mistakes.
What Makes a C3PAO Valuable
A competent C3PAO has excellent comprehension of the CMMC requirements and the DoD’s evolving expectations. Look for assessors with prior defense sector experience, a clear understanding of NIST SP 800-171 controls, and a reputation for transparency and collaboration.
Investing in Expertise Pays Off
Hiring outside help may seem like an added expense, but failing an audit—or losing contract eligibility—can cost far more. A modest investment now can protect future revenue, strengthen your security posture, and speed up certification.
Smart contractors know when to ask for help—and doing so could be your strongest competitive edge.
Common Technical Gaps Exposed by Early Audits
As more defense contractors undergo pre-assessments and CMMC readiness checks, recurring technical issues are surfaced across the board.
- Outdated Systems and Unsupported Software
Many contractors still rely on legacy systems that no longer receive security patches or updates. These outdated environments are prime targets for cyberattacks and fail to meet even basic cybersecurity hygiene requirements.
- Weak or Incomplete Documentation
An alarming number of companies submit System Security Plans (SSPs) that are either outdated, incomplete, or poorly structured. Without clear documentation that maps security controls to NIST SP 800-171 standards, passing a CMMC audit becomes nearly impossible.
- Inadequate Incident Response Planning
Organizations frequently lack a tested and documented plan for identifying, reporting, and responding to security breaches. This is a critical shortfall that directly impacts their ability to meet Level 2 compliance requirements.
Lay the Groundwork Today, Secure the Future Tomorrow
CMMC compliance is more than a requirement—it’s a chance to fortify operations and gain a competitive edge. Early preparation helps uncover weaknesses, strengthen internal processes, and reduce the risk of disruptions.
Taking action now sets your business apart, builds trust with DoD partners, and ensures continued eligibility in an increasingly security-focused ecosystem. Waiting is the real risk—leaders who act early will lead the future.

Recent Comments